In the fast-paced digital world of 2025, where cloud platforms, IoT devices, and remote operations dominate, one silent threat continues to evolve, DNS amplification attacks. These attacks might not make headlines every day, but when they strike, they can cripple entire organizations, disrupt services, and cause millions in damages within minutes.
In this blog, we’ll break down what DNS amplification attacks are, explore how they’ve evolved, examine their growing impact on businesses, and discuss practical defense strategies for cybersecurity professionals.

What Is a DNS Amplification Attack?
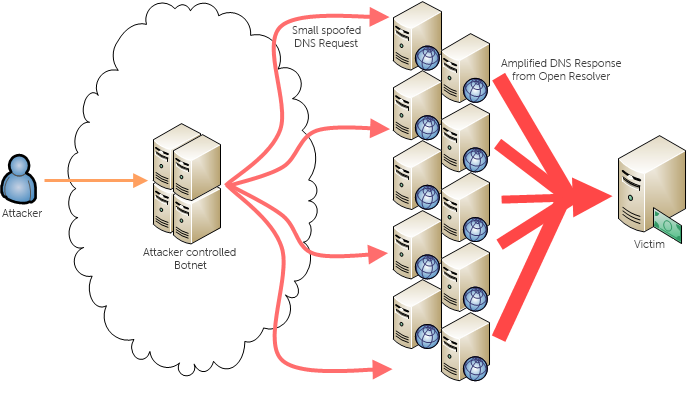
A DNS amplification attack is a type of cyberattack that abuses the Domain Name System (DNS). The internet’s phonebook that turns website names into IP addresses. Attackers send small DNS requests but fake the sender’s address so the reply is sent to their target instead. Because DNS responses are much larger than the original request, this process “amplifies” the attack, flooding the victim’s network with massive traffic. With just a few requests, hackers can overwhelm servers and cause large-scale service outages.
Why Does It Matter in 2025?
In 2025, DNS amplification attacks have become more dangerous and sophisticated than ever. The rapid expansion of cloud infrastructure, IoT devices, and open DNS resolvers has widened the attack surface for cybercriminals. Armed with AI-powered tools and easily rented attack kits, hackers can now launch larger, smarter, and more cost-effective assaults. According to Cloudflare’s 2025 report, DNS-based DDoS incidents have surged by more than 40% since 2023, leading to millions in financial losses and reputational damage. As our interconnected world grows, securing DNS systems is no longer optional—it’s a critical priority for every organization.
How DNS Amplification Attacks Work: A Step-by-Step Breakdown
To understand how attackers weaponize DNS, let’s look under the hood.
Step 1: Spoofing the Source IP
The attacker begins by sending a DNS query to an open or misconfigured DNS resolver (a server that responds to DNS requests). However, instead of using their own IP address, they spoof the victim’s IP address, tricking the server into thinking the request came from the target.
Step 2: Sending Small Requests
The attacker sends very small queries that will generate large responses, like asking for all DNS records of a domain using a command like.
Step 3: Amplification
Here’s where the magic or rather, the mayhem happens. The DNS server sends back a response that’s dozens or even hundreds of times larger than the original query. For example, a 60-byte request might trigger a 4,000-byte response.
This is known as the amplification factor, and it can grow to 50–100 times larger than the initial query.
Step 4: Overwhelming the Target
Because the response is sent to the spoofed IP, the target’s server or network is hit with an enormous amount of traffic so much that legitimate requests can’t get through.
Step 5: Sustained Attack Through Botnets
Attackers often use botnets, networks of infected devices, to automate and scale this process, creating distributed attacks that are difficult to trace or stop.
The Impact of DNS Amplification Attacks on Organizations
The impact of a DNS amplification attack can be crippling for any organization. Beyond just slowing down a network, these attacks can shut down services, interrupt operations, and cause lasting financial and reputational damage. Below are some real-world examples and common consequences businesses face when such an attack succeeds.
- Massive Downtime: Businesses lose access to critical systems and customer-facing platforms. In 2024, a European fintech startup reported over $1.5 million in losses after a 12-hour DDoS outage caused by a DNS amplification attack.
- Collateral Damage: ISPs and cloud providers can also be affected, especially if attackers use shared infrastructure or public resolvers.
- Data Breaches and Reputation Loss: While DNS amplification itself doesn’t steal data, it often serves as a distraction for other attacks happening simultaneously, like data exfiltration or ransomware installation.
- Financial and Compliance Risks: For regulated industries like finance and healthcare, downtime can lead to compliance violations, customer trust issues, and legal penalties.
The Evolution of DNS Amplification Attacks Up to 2025
DNS amplification isn’t new, it’s been around for over a decade, but the tactics, scale, and technology have evolved dramatically.
Rise of Reflection-as-a-Service (RaaS)
Just like ransomware evolved into “Ransomware-as-a-Service,” 2025 has seen the rise of Reflection-as-a-Service models on the dark web. Attackers can rent DNS amplification kits or botnets with ready-to-use tools for as little as $50 per hour.
Exploitation of IoT Devices
Many IoT devices (like routers and cameras) are still shipped with default DNS configurations, making them ideal candidates for being hijacked into botnets.
Hybrid DDoS Attacks
Modern cybercriminals combine DNS amplification with application-layer (Layer 7) attacks to create multi-vector assaults that are harder to mitigate.
AI-Driven Attack Automation
Artificial intelligence tools are now being leveraged to identify vulnerable DNS servers automatically, optimize amplification ratios, and evade traditional mitigation systems.
Preventive Measures and Best Practices
So, how can organizations protect themselves? The good news is that DNS amplification attacks are preventable. If you follow layered and proactive defenses.
a. Disable Open DNS Resolvers
Ensure that your DNS resolvers do not respond to queries from unauthorized sources. Implement Access Control Lists (ACLs) to limit who can query your server.
b. Implement Response Rate Limiting (RRL)
RRL restricts how many identical responses a DNS server sends within a given time frame, minimizing amplification potential.
c. Source IP Verification
Routers and firewalls should use BCP 38 (Network Ingress Filtering) to block packets with spoofed source addresses before they reach your network.
d. Keep DNS Software Updated
Outdated DNS software often contains vulnerabilities that attackers exploit. Regularly patch and monitor software like BIND, Unbound, or Microsoft DNS.
e. Deploy DDoS Mitigation Solutions
Invest in cloud-based DDoS protection services (like Cloudflare, Akamai, or AWS Shield) that can absorb and filter malicious traffic before it hits your infrastructure.
f. Continuous Monitoring and Threat Intelligence
Use SIEM solutions such as Splunk or Microsoft Sentinel, integrated with threat intelligence feeds, to quickly identify and respond to abnormal DNS traffic patterns.

Technological Advancements in Mitigating DNS Amplification Attacks
The cybersecurity landscape isn’t standing still—several innovations are reshaping how we combat DNS-based threats.
DNSSEC and Zero Trust
While DNSSEC (Domain Name System Security Extensions) primarily protects against spoofing, its integrity features also reduce opportunities for abuse in amplification attacks.
In combination with Zero Trust Architecture, DNSSEC ensures only verified devices can query internal servers.
AI-Powered Anomaly Detection
Modern AI-driven platforms use machine learning to analyze billions of DNS queries in real time, flagging abnormal traffic spikes that could indicate amplification attempts.
Edge Security and Anycast Networks
Companies are increasingly adopting Anycast routing, where multiple servers share the same IP globally to distribute traffic efficiently. This not only improves performance but also absorbs DDoS floods more effectively.
Threat-Sharing Communities
Cybersecurity alliances like FIRST, Shadowserver, and CERTs collaborate globally to identify and take down vulnerable DNS servers, reducing the overall attack surface for everyone.
Conclusion: Staying Vigilant in a Hyperconnected World
DNS amplification attacks remind us that the internet’s very foundations, DNS can be weaponized when security is overlooked.
In 2025, as networks grow more complex and interconnected, awareness and proactive defense are key. Organizations must treat DNS not as a background service but as a critical security asset. By implementing rate limits, filtering spoofed traffic, and leveraging AI-driven defense tools, businesses can stay one step ahead of attackers.
Ultimately, defending against DNS amplification isn’t just about technology—it’s about fostering a culture of vigilance, continuous learning, and global cooperation among IT professionals.
Because in cybersecurity, the best defense is preparation, and the best time to prepare is now.
